BY CAROLYN CARTER, FLUKE NETWORKS
Wireless local area networks (LANs) are always in one of the four distinct but interrelated phases of the wireless lifecycle. Adopting best practices in each of these four phases will enable faster deployment, higher performance and greater security of the wireless LAN, all of which equates to greater satisfaction from network users. These phases are 1) predeployment and expansion planning, 2) installation and verification, 3) troubleshooting and security, and 4) management and optimization. In this article I will describe the considerations that network administrators should take during each of the four phases in order to ensure their wireless LANs are operating effectively and efficiently.
If you are building a wireless LAN from scratch, you are in the predeployment phase. Existing network managers are always analyzing what they need to meet user requirements and what devices may need to be added to the network to accomplish that. As such, the existing network is also in an expansion-planning phase.
Once needs are defined and the technologies required to meet those needs are identified, deployment begins–putting the network in the installation and verification phase of the lifecycle. Once a network (new build or expansion) is deployed, running and verified, its users are on it. This puts the network into the troubleshooting phase, which hopefully is brief. In this phase, network administrators address and correct issues as quickly as possible, sending the network into the phase of maintenance and optimization. In reality, while a wireless network is in use it will frequently go back and forth between the troubleshooting and maintenance-and-optimization phases. At some point the users will outgrow the network and need to redesign or expand. When that happens, the cycle begins anew with predeployment and expansion planning. So no matter what the state of your wireless network, you are in one of these four phases.
When designing a wireless LAN it is important to understand user needs and design accordingly. One key consideration is whether the wireless LAN is a network of convenience or of necessity. A network of convenience can be characterized as one in which users' primary activities are using email and accessing the Internet. In these cases the wireless LAN is not mission-critical to the organization.
These networks of convenience are becoming fewer and fewer today, especially with the introduction of IEEE 802.11n and higher-capacity networks. Organizations are moving toward mission-critical wireless LANs, or networks of necessity, which support daily operations and high-demand applications. Mission-critical networks have more requirements than networks of convenience, making it crucial to understand the extent of your needs before designing a wireless LAN.
Another important consideration is future requirements. Many network owners only think about current needs and requirements when planning a new network build or network expansion. In as little as six to twelve months those needs may expand and if future needs were not considered initially, a network administrator may find itself with a recent investment that does not fulfill current needs. So when planning a wireless LAN, be sure to look at the requirements for the network you will operate in the future as well as what you're operating today.
The perils of interference
Many people do not realize the effects that interference can have on a wireless network. 802.11-based wireless networks operate in the unlicensed frequency band between 2.4 and 2.5 GHz. "Unlicensed" means any device is allowed to operate in the band. Because there are no restrictions, there is a lot of interference between 2.4 and 2.5 GHz, including microwave ovens, cordless phones, Bluetooth devices and in some cases security devices such as cameras and motion sensors.
The reason interference is a significant issue in wireless LANs is that 802.11-based networks use a polite protocol. If the protocol hears another device communicating, it will not communicate. In the case of interference, when the wireless LAN protocol is talking, the interferer will essentially talk "on top of" the wireless LAN signal and that signal will not get through to its intended destination. It will retransmit many times and in doing so, degrade the system's throughput. Interference is a significant culprit here, as more than 60 percent of wireless LAN problems are interference-based.
Before designing your network, conduct a survey for interference. At the predeployment stage, the types of interferers you'll be able to detect are fixed points, such as microwave ovens. Devices that create interference only infrequently may not be detected and as a result cannot necessarily be designed against in initial network planning. Even so, network planners do need the ability to find these types of interferers when they are active.
A few means are available for detecting interference. Some infrastructure providers include spectrum analyzers with their wireless access points. Another option is to use handheld spectrum analysis tools. In either case, when you have an interference issue you must get rid of it. There are three options.
- Find the interfering device and remove it.
- If you cannot remove the interfering device, physically shield around it so it does not cause interference with your wireless LAN.
- If you cannot remove or shield around the interfering device, reconfigure either the wireless system or the interfering device.
Unless an interfering device is well-documented at the very least, it will continue to cause problems.
Channel mapping a challenge
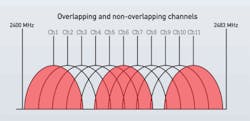
Channel mapping for a wireless LAN can be confusing and if not performed correctly, can degrade the network's performance. Many users are challenged to correctly channel-map their wireless LANs. In the 2.4-GHz operating band are 14 channels. In the United States only 11 of those 14 channels can be used. And only three of those channels do not overlap with at least one other channel. The de facto non-overlapping channels in the U.S. are 1, 6 and 11. (Contrast that with the 5-GHz band, in which there are 38 channels, none of which overlap. Of the 38 channels, 34 can be used in the U.S.)
In order to effectively channel map your wireless LAN, you will need to know which channels you will use, which channels you are considering using, and which channels your neighbors are using. Channels in the 2.4-GHz band are approximately 20-MHz wide and are spaced approximately 5-MHz apart. As the illustration on page 28 shows, channels 1, 6 and 11 (in red) are the only three that do not overlap with any other channel. Areas where there is overlap are referred to as adjacent channels; they cause rather severe interference that will cause significant problems for a wireless LAN.
Controlling or eliminating adjacent channels, unfortunately, is not entirely in the hands of a network administrator. For example, even if a wireless LAN uses the non-overlapping channels 1, 6 and 11, a neighbor using channel 3 will create overlapping channels, causing interference between neighboring networks. Both networks' throughput will be compromised.
Often wireless LAN equipment will include software that controls channel use. If that is the case, make sure the system is following the correct channel patterns. Many times I have found access points on channels 1, 6 and 11 as expected, but also found them on other channels such as 3 and 7. The point is, wireless LAN infrastructure systems that control channel use do not always keep every access point on the non-overlapping channels. It remains the responsibility of the network administrator to avoid interference caused by channel overlap.
Designing the network
Having determined the type of network you will deploy and accounted for as much interference as possible, it is now time to design the network. Some designers still use the time-consuming method of the pencil-and-paper walkthrough that results in hand-drawn network maps. However, infrastructure-planning tools that are now provided with most wireless LAN systems, as well as bundled with site survey tools, are a more-efficient approach. These tools allow you to simulate radio-frequency (RF) conditions in a number of different environments.
Whether the facility is a warehouse with a lot of metal racks, a hospital with many walled-off rooms and areas, or any other physical environment, software-based simulation tools allow you to simulate the impact of that physical environment on wireless LAN transmission, and plan accordingly. These tools also all you to play the "what-if" game, as in, what if I put access point number one here, access point number two there, and so on? Or, what if a wall gets built in this particular spot? These tools also allow you to purchase appropriate equipment to meet current and future needs, by calculating the effects of additional users and additional applications such as Voice over WiFi.
As you certainly know, there are many wires behind a wireless network. That is why an important part of the wireless-LAN design process is to verify the structured cabling system. Cabling that does not function properly because it is damaged or low quality may not adequately support a mission-critical wireless LAN. So at the very least qualify your cabling plant to Gigabit Ethernet requirements, or be safe and conduct a full certification.
Post-deployment verification
Even after all the planning, predeployment testing, network design and the actual installation of the wireless LAN, the job is not completed. A couple issues may creep up. Namely, just because a site-survey planning utility or infrastructure-planning utility says a network would work correctly, it does not absolutely guarantee that the up-and-running network will meet all user requirements. For that reason, we recommend that after deployment and before the network is fully populated with users, you conduct a verification survey to see if the deployed network meets all requirements.
You can conduct either a full site survey or a spot survey/spot verification. Spot verification is the easier of the two. To conduct the survey, walk from one area to another within the facility verifying that you can see all your networks as well as the access points you expect to see. If you cannot see an access point that you should see, then you have uncovered an issue. This type of survey allows you to check your coverage as well as signal strength. A product such as Fluke Networks' AirCheck will enable you to conduct this type of spot survey, as well as troubleshooting.
However, simply seeing the network or its access points does not necessarily mean that you can connect to it. A full site survey is a more-comprehensive approach for post-deployment verification. In a full site survey, you will connect to all access points and service set identifiers to ensure you can get into the network and there are no firewall problems. You can also verify channel use and determine if you have too many users on a certain channel. And once again, you have the opportunity to conduct an interference check. It is possible to see interferers at this time that you did not see in your predeployment checks, especially considering a lot of interference is intermittent.
Full-scale, comprehensive site survey packages like the AirMagnet Survey Pro available from Fluke Networks conduct active testing and include features such as heat maps, which document verification results for your records. A benefit of these heat maps is that if you have a problem later, you can check the previous maps to see what has changed. Including spectrum analysis in a post-deployment survey allows you to have complementary heat maps and spectral maps for full network documentation.
Regardless of which phase of the wireless lifecycle your network is in, two things are certain: Sooner or later the network will move to the next phase, and verification as well as documentation and troubleshooting tools exist to make the transition from one to the other as smooth as possible.
CAROLYN CARTER is product manager for portable network tools with Fluke Networks (flukenetworks.com).