If the promise of IP-based convergence comes to fruition, how will security applications like access control fit in?
"Convergence” is a term that’s used widely in today’s networking environment. But what does it mean? According to Rich Anderson, president of Phare Consulting (www.phareconsulting.com), a management consulting firm serving high-tech business-to-business companies, “There are as many definitions of convergence as there are authors of articles on convergence.”
Access-control products and systems have bridged the performance gap and are on their way to interoperability, enabling open-system architectures.
Anderson has a long history in the security industry, having served in more than one vice-presidential role within the GE organization, including GE Security’s enterprise group. He gave his tongue-in-cheek, yet quite accurate, assessment of convergence in a presentation at the ISC West conference in April. The conference focused on all levels of security in the enterprise.
In his presentation, “The coming convergence revolution: How IP access control will change the security industry,” Anderson listed common definitions of “convergence”-all of which combined physical security with information technology (IT)-before offering up his own definition.
Convergence, he says, is a single solution to common problems. Incorporated within that notion are such actions as taking common approaches to common threats to security and IT functions, effecting tight cooperation among all security professionals, eliminating redundant systems and technologies, and standardizing technology platforms. Other actions may include common security management and a merger of the IT and security industries. All are part-and-parcel of security/IT convergence; not one of them in and of itself can realistically be called convergence.
Convergence then, Anderson says, is the adoption of a holistic view for the security threats facing an enterprise.
Several market forces are pushing enterprises to converge their security and IT functions. But as Anderson points out, there are just about as many forces pushing back.
Pushing toward convergence
Four dynamics in the security and IT industries are pushing the two worlds toward each other:
• Technology is merging. New security systems are based on IT technology (network cameras are a prime example). On the business side of the equation, security departments cannot afford their own IT groups.
• Corporations’ political climates are giving rise to the probability of convergence. Boards of directors are under significant pressure to be watchful of their organizations’ activities. The infamous Enron and Tyco debacles were met with swift legislative action in the form of the Sarbanes-Oxley Act of 2002. As Anderson said at ISC, what follows within corporations is the need for “one-throat-to-grab.” The ability to place responsibility, if not with a single individual, then with a single department, is attractive to a company’s executives.
•Overlapping activity. Identity management may be the most common example. For example, access-control systems by which an employee gains entrance to a facility include records of each user’s dates and times of entrance. Records for all employees/users are maintained in a database that, in all likelihood, is housed on the corporate network. Futhermore, after using some form of access to enter the facility, each employee uses a separate access code (password) to log on to the corporate data network. The potential for combining these and any other access-control functions suggests that cost savings are there for the having.
Corporations’ security and IT functions face similar threats. “Many who would like to harm a company really don’t care what department they inconvenience,” Anderson said in his address. Theft of company data and assets is the real issue, and as Anderson added, it doesn’t matter if the attackers violate a firewall or steal backup tapes from a delivery service. Two separate lines of security-one for IT functions and another for the physical premises-unfortunately, provide more opportunities for intrusion, not fewer.
Pushing back
But four just as significant dynamics are essentially working to resist convergence:
• First and perhaps foremost, the two functions exist in different cultures. The lack of respect between security and IT is legendary, as Anderson pointed out. Merging the two groups would require a significant amount of cooperation, which will not come easily.
• From a practical standpoint, the two groups own different knowledge sets. While IT groups, generally speaking, possess more technical knowledge than security groups, physical security systems managers possess unique skills in such applications as access control and closed-circuit television. Importantly, neither group could easily or quickly acquire the other’s established skill set.
• Third, convergence carries with it the probability that one group will suffer a loss of control, particularly with respect to budgets. Physical security department managers fear the loss of control over equipment budgets.
• Finally, politics come into play, just as in the push toward convergence. On this side of the issue, however, the aforementioned culture clashes likely will lead to internal political turf wars as pressures mount for risk and expense reduction.
Anderson believes two main factors will give the forces for convergence the victory over the forces against: The opportunity to save money and the reduction of risk.
Today's access-control systems include a substantial amount of proprietary wiring and hardware, which could very well be eliminated if and when IP-based access control emerges.
Overlaid onto the scenario of security and IT convergence is the current state of access-control technologies and products for access control. which are shifting from being proprietary in nature to being able to exist in an open-architecture environment.
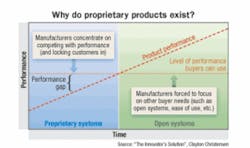
In very general terms, products naturally improve all the time. At some juncture, however, the products reach a point at which users do not need or cannot use the latest technological advancements. Anderson used Microsoft Word as an example: How many people even know, much less use, all the features of Word’s latest edition?
Early in a product’s lifecycle, Anderson explained, it has a performance gap; products struggle to meet users’ needs, and these products’ manufacturers focus on performance. In such cases, proprietary products are the best solutions. Cabling industry veterans will recall the early days of customer-owned cabling systems, before Telecommunications Industry Association (TIA) standards specified their construction and performance. At that time, single-vendor proprietary systems were the only option. But years later, professionals in the cabling industry have become accustomed to interoperability, from which open systems can be constructed.
Today’s access-control systems are still on the proprietary side of the ledger, but have effectively closed the performance gap. In other words, the access-control systems now available meet the functional needs of their users. This kind of achievement is something of a tipping point in a product set’s lifecycle; once meeting users’ basic needs, manufacturers focus on other needs, such as ease of use or open systems technology.
Meanwhile, other business and technical forces push manufacturers toward creating open rather than proprietary systems. Namely, new manufacturers enter the business and end-user organizations begin to demand open systems in which multiple manufacturers’ products can be used. Within those organizations, as described earlier, are increasing pressures from upper management to reduce risk and cost.
All the while, technology is advancing in other realms, including, of course, IT. Companies that manufacture access-control and other security products also experience pressures that push them toward creating open systems. Specifically, there is pressure to reduce research-and-development costs and time-to-market, end users are demanding economical and open solutions, and there’s always the need for business growth.
Anderson concludes that access-control systems would appear to be on the path toward open-system architecture. In his presentation, he estimated 2010 for the widespread use of open-system architectures for access-control systems.
For what could very well be the converged security/IT discipline in 2010, the upshot of open-architecture, access-control systems will be the elimination of proprietary wiring between system elements. Other consequences will include the commoditization of access hardware, the emergence of IT suppliers as the primary providers of access-control software, and having IT knowledge as a prerequisite for success in access-control system deployment. Other likely derivatives of these market forces include more widespread deployment of access control because of lower costs per door.
Keys to success
Anderson delivered his message to a gathering of security integrators-those whose livelihoods are made by providing end-user organizations with design and installation services for security systems, including access control. To this group, he stressed that they must become IT integrators. Training and practical experience in software management will be the key to success.
And that’s what trained professionals in the security industry have to offer current and prospective customers-experience and expertise in the security applications that have become so critical to user organizations. Not all security products will become commodities, Anderson noted, and those highly engineered solutions will require security-systems expertise to perform optimally.
While it seems like the whole world is talking about convergence, many business, technical, and political issues require addressing before security and IT functions come together. Those with a long history of integrating security systems bring a wealth of experience and expertise to this impending convergence, and also face the challenges of blending their trade with that of the IT profession.PATRICK McLAUGHLIN is Chief Editor of Cabling Installation & Maintenance.